Which NVM works best in mobile payments, IoT and other applications.

One-time programmable (OTP) memory is a type of non-volatile memory (NVM) that commonly comprises of electrical fuse (eFuse) and antifuse. The advantages of OTP memory over multi-time programmable (MTP) memory, such as EEPROM or flash memory, are smaller area and no additional wafer processing steps. Therefore, for many low-cost applications, the OTP memory is used to replace the MTP memory.
However, there are also differences within OTP between eFuse and antifuse, such as programming mechanism, security, and power consumption. In terms of programming mechanism, an antifuse is programmed by electrically shorting the gate and source of a transistor with an avalanche breakdown when a high voltage is applied to the thin gate oxide. In contrast, an eFuse is programmed by electrically blowing a strip of metal or poly with a flow of high-density current using I/O voltage.
The low resistance metal in eFuse is blown by electro-migration (EM) because the high-density current flows through a narrow metal or poly. A bone-type layout is commonly used for eFuse (see Fig. 1 below).

Figure 1. A programmed poly eFuse. Source: MA-Tek
During the programming operation, the larger-width area in the two terminals of the eFuse has a better cooling effect than the narrow-width area in the middle of the eFuse. Therefore, the blown portions of eFuse are always in the narrow-width area in the middle of the eFuse. Furthermore, to program one bit requires a pair of eFuse layouts—one for programming and the other for the reference resistor of the differential sense amplifier. eFuse can only be programmed one time to be a ‘1’. If the eFuse cannot be read as a ‘1’ after programming, then the programming failed, which means yield loss. Antifuse, on the other hand, can be programmed ~18 times to be a ‘1’. If the antifuse cannot be read as a ‘1’ after the initial programming, then it can be programmed again and again, which improves the yield.
In relation to security, antifuse is better than eFuse because there is no visible difference between a programmed bit and unprogrammed bit. Traditionally, in the polysilicon-gate CMOS logic process, poly eFuse is very popular (Figure 1) and the EM occurs in the silicide layer. However, in the new generation of high-k metal gate ( HKMG) CMOS logic process — developed to reduce the leakage of MOSFET — there is no polysilicon layer to be used as eFuse. Therefore, a different type of eFuse produced by Intel is implemented as metal 1 traces is shown in Figure 2.

Fig. 2. A programmed eFuse in the Westmere/Clarkdale processor produced by Intel. Source: Custom Analysis of the eFUSE Structures used in the Intel Westmere Clarkdale 32nm Processor, TechInsights
In Figure 2, there are four pairs of eFuses formed in metal 1 and two eFuses are blown. There is a total of two blown eFuses and six intact eFuses, along with interconnects to the underlying drive transistors. The blown portions of the eFuse have irregular shapes and are easily visible. In Figure 3 below, there are four pairs of eFuses formed in metal 2 and two of the eFuses are blown. Figure 4 also shows a pair of eFuses. Again, the blown (or programmed) eFuse is easily detected.

Figure 3. A programmed eFuse in TSMC eFuse 20 nm planar HKMG process. Source: Qualcomm Gobi MDM9235 Modem 20 nm HKMG Logic Detailed Structural Analysis, TechInsights.
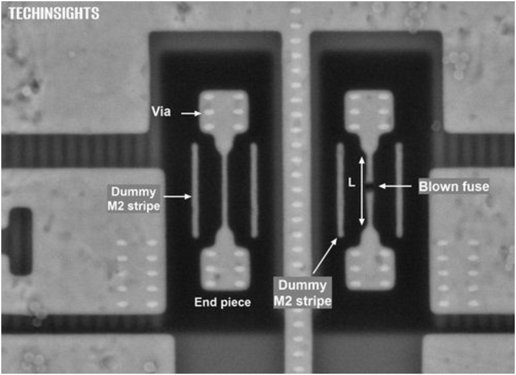
Figure 4. Enlarged view of the programmed TSMC eFuse. Source: Qualcomm Gobi MDM9235 Modem 20 nm HKMG Logic Detailed Structural Analysis, TechInsights.

Figure 5. A programmed antifuse. Source: http://archive.eettaiwan.com/www.eettaiwan.com/emag/1302_15_DC.html, Kilopass.
In Figure 5, an antifuse is programmed, but, in contrast with eFuse in the previous examples, there are no blown portions to be found in the cross-section or the top view, and there is no hot spot in the voltage contrast FIB. This makes it very difficult for unauthorized users to obtain the contents of the data stored in the antifuse memory.
With respect to power consumption, antifuse uses less power in the unprogrammed state as compared to eFuse. The typical resistance value of an unprogrammed eFuse is approximately 50 to 100 ohms, while the typical resistance value of a programmed eFuse is approximately 10Kohms to 100Kohms. An antifuse is the opposite. The resistance of an antifuse is higher in the unprogrammed state. The default value of an unprogrammed bit is ‘0’ so it is necessary to only program the bits that are ‘1’. Therefore, the more ‘0’ stored in the eFuse, the more power is consumed. In contrast, the more ‘0’ stored in the antifuse, the less power is consumed. In addition, the standby power, or leakage, is much higher for eFuse than for antifuse.
In summary, an OTP memory with antifuse has better yield for programming, lower power consumption for unprogrammed bits, and overall superior security. Therefore, an OTP memory with antifuse is more suitable for mobile payments, Internet of Things (IoT), and other applications than OTP memory with eFuse.
Very good summary. Adding some circuitry would be nice too.
I’d like clarification on this comment – “ Antifuse, on the other hand, can be programmed ~18 times to be a ‘1’. If the antifuse cannot be read as a ‘1’ after the initial programming, then it can be programmed again and again, which improves the yield.” What’s the reasoning to the ~18x times programming limit? Does reliability suffer beyond 18x?
As they are different mechanisms I don’t think you can equate them like that, and I would phrase it differently – zapping a fuse results in almost a sure-fire bit-flip. Zapping an OTP cell does not – you may have to hit it several times (this can be a pain on a production ATE system). It’s not an advantage – it’s a workaround for the inherent variability in the antifuse process. After the recommended 18 zaps, you have probably damaged the cell to the point where it is never going to flip, so you might as well give up. I would guess the 18x comes from characterising many cells and setting (say) a 99.99% limit on programming success. All is not lost – you can still use built-in spare cells to tag the faulty location and repair it when you read the OTP.