Security risks of common IC test strategies and how to mitigate them.

Applications like as smart cards and devices used in the defense industry require security to ensure that sensitive data is inaccessible to outside agents. This used to be a niche requirement met through custom solutions. However, now that automotive and cyber-physical systems are proliferating, the requirements around secure test and monitoring are becoming mainstream. The current best strategy is to add security across different levels of SoC development to provide the best coverage in a defense-in-depth solution. Figure 1 illustrates a high-level concept of device security across the ecosystem.

Fig. 1: Siemens defense-in-depth solutions.
The implementation of test structures, which falls under System Integrity in figure 1, can significantly compromise any functional security features already part of the design. Let’s look at the security risks of common IC test strategies and how to mitigate them.
Scan chains provide full access to the sequential elements of a device under test. Serial access from device pins allows test patterns to provide the stimulus and response needed to detect defects.
While fully accessible scan chains are great for test, they aren’t great for security because they allow easy access to any portion of the device. For secure applications, the industry needs alternate approaches that provide the benefits of deterministic scan test while maintaining the required IC security.
In addition to scan chains, most designs now have some form of test access mechanism (TAP). This can be a simple external interface such as IEEE 1149.1 (JTAG), or it can be both an external and internal interface with an in-system test controller is used for running in-system test.
The TAP is mostly used for setup, configuration, running and data collection of various complex test structures within the design. Once enabled, the TAP gives direct access to many critical registers within the design, putting sensitive data at risk or, in some cases, causing the device to operate outside it’s intended function. To keep the TAP from acting as a simple back door to security threats, it must be as secure as the other functional interfaces within the design. Figure 2 shows how with a JTAG TAP based test access mechanism (TAM), there can be several vulnerable points that are open to attack, both externally and internally.
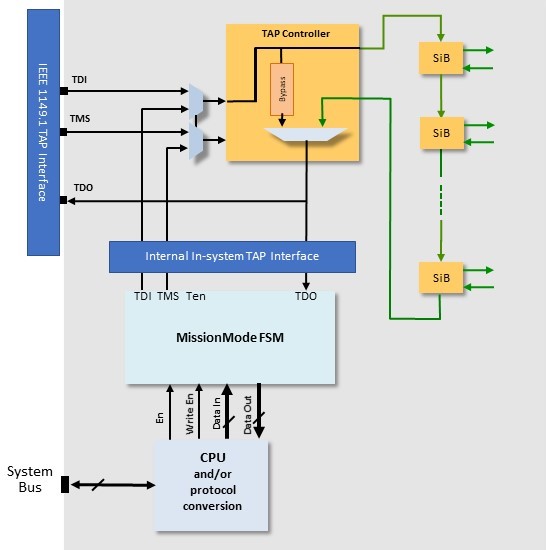
Fig. 2: Typical JTAG TAP-based TAM.
There are approaches to IC test that are better from a security point of view. Functional patterns ensure the device works as designed and meets its functional specifications. While difficult and time-consuming to create, function patterns are used for secure applications because they can be created in a closed environment by the chip design team and applied in a secure tester environment.
Built-in self-test (BIST) is more secure test technique because it uses a pseudorandom pattern generator (PRPG) embedded in the circuit to create patterns on chip and apply them through the design’s scan chains. An on-chip BIST controller controls the number of patterns, shift cycles, and other parameters that allow the test to be fully contained inside the device. An external start signal launches the test and the final unique signature is scanned out. Given this simple interface, logic BIST is ideal for applications requiring in-system test capabilities where the test logic can be controlled through a simple board-level access such as a JTAG TAP controller.
For scan test, a secure embedded test compression provides the benefits of deterministic scan test while meeting the security requirements of secure applications. Working with test compression is a new method of distributing scan test data across a bus-based system, which enables simultaneous testing of any number of cores even with few chip I/Os. This bus-based packetized test reduces test time by enabling high-speed data distribution, by efficiently handling imbalances between cores, and by supporting testing of any number of identical cores with a constant cost. A basic bus-based scan data delivery architecture is shown in figure 3.

Fig. 3: Basic bus-based packetized scan data architecture.
The bus-based scan data distribution also adds a level of security on top of embedded test compression because access to the scan chains has an additional level of abstraction. The scan data are bussed around the SoC, removing the direct access from the external pins to the scan channels. The data transferred to and from internal scan chains is both compressed and packetized to be delivered over the test bus.
Bus-based scan data distribution also supports on-chip compare. On-chip compare ensures that no data that has passed through the functional flip-flops can be taken off-chip because the actual checking of the ATPG result is done on chip. This removes the need for any data from the scan flops to ever be taken off chip. This adds another level of security because no data that has touched internal functional logic is ever taken off chip. The pass/fail result from the on-chip compare is stored in a status register, which is not part of the functional logic and is typically read by the IJTAG infrastructure.
Finally, for secure ICs, designers need to look at a secure test access mechanism (TAM), which is typically JTAG on today’s SoC. The TAM enables functional debug modes within the device and could also be mapped in some places to the functional address map, so it is critical that this interface has a high level of security protection.
In the past, the solution to securing the TAM has been to either not bond the JTAG pins in the production package, or to disconnect the test access port (TAP) after the device has completed final test. However, with the increasing need for in-life analytics data collection and customer return analysis for SoCs in automotive and safety applications, we need access to the internal test network either externally or through an embedded safety island and on-chip security manager socket.
It is possible to implement a number of different layers of security, so that different keys can unlock the device to different levels, granting different access rights for various applications or users. This approach is used extensively in the automotive ecosystem. Figure 4 shows scenarios where different levels of access would be appropriate.

Fig. 4: Different levels of access to the chip can be granted at different stages of the chip lifecycle.
SoCs for secure applications, including automotive and medical devices, need special attention to risk mitigation during design and in-life operation. Deploying all of the security technologies discussed here and more builds multiple rings of defense. Using existing test technology to introduce many levels of protection can provide a significant defense against malicious attacks. Although some of these concepts are passive—they just providing a lock against access—others are also reactive in that they can take evasive action when a threat is detected.
Leave a Reply