No-click and blockchain attacks point to increasing hacker sophistication, requiring much earlier focus on potential security risks and solutions.

Cyberattacks are becoming more frequent and more sophisticated, but they also are starting to compromise platforms that until recently were considered unbreakable.
Consider blockchains, for example, which were developed as secure, distributed ledger platforms. All of them must be updated with the same data for a transaction to proceed. But earlier this year a blockchain bridge platform called Wormhole — which connects different blockchains to make crypto currency transfer easier — was hacked. The thieves made off with $324 million worth of crypto assets. In Q1 2022, total blockchain hacks amounted to $1.3 billion.
Additionally, on March 29, 2022, $620 million in Ethereum was stolen by the Lazarus Group and APT38, cyber-criminal organizations linked to North Korea, according to the FBI. The U.S. State Department’s Rewards for Justice (RFJ) program offers rewards up to $5 million for information that helps disrupt that country’s cybercriminal activities.
Hackers are coming up with new tricks as demonstrated in the “zero-click” attack case. Most people are aware of the different phishing schemes and have learned not to click any links that look suspicious in emails or texts. Yet hackers are finding ways to breach security by spotting operating system flaws and vulnerabilities in iPhones, Android phones, and PCs. For example, hackers can access banking information stored in mobile phones even when users do not click.
The solution, according to Jen Easterly, director of the U.S. Cybersecurity and Infrastructure Security Agency, is “preparation, not panic.” That sounds simple enough, but that preparation can be a big challenge.

Fig. 1: There are three security layers in designing a network system — technology (red), application (orange), and management (purple). Source: CompTIA.
Secure building blocks
So is it possible to build an “unbreakable” system? The answer is yes, but you probably don’t want one. A closed and isolated system is 100% secure, but as soon as it is connected to the internet it’s open to cyberattacks.
In most cases, the better alternative is to build secure systems from the ground up. Connected hardware devices with a full stack of software are considered a baseline for most applications. Data from multiple sources needs to be generated, processed, and stored, and the common threads for securing that data are building-block security and end-to-end security.
The components used in electronic systems need to be secure, and so does the supply chain for the hardware and software used to build those devices. Component suppliers must be managed so that no counterfeit parts and software are used. In addition, the manufacturing process should have procedures in place to prevent introducing malware or errors to devices. If the supply chain is not secure, the device will not be secure, and anything connected to it — including the network — will be vulnerable.
“Nowadays the industry is focused on managing risk in the software supply chain,” said Jonathan Knudsen, head of global research at Synopsys’ Cybersecurity Research Center (CyRC). “The software supply chain includes everything from the idea for an application through to its use by humans or machines. The supply chain includes obvious things like open-source software components and deployment base images, but also development tools, component repositories, build systems, source control systems, and more. The best way to get started is to think holistically. What level of risk is acceptable? What contributes to that risk? How can you mitigate risk across the supply chain?”
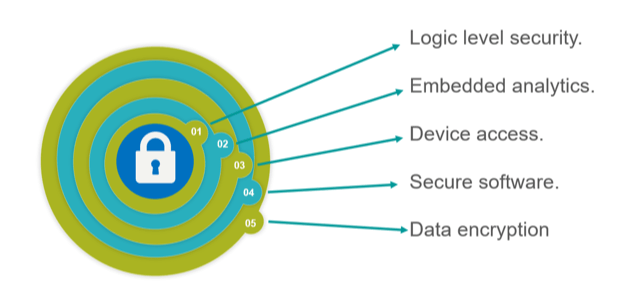
Fig. 2: A secure, embedded system includes layers of protection starting with the logic level. Source: Siemens EDA
“A well thought out security approach is a layered solution, which could encompass any of the above technologies, or even all of them with the foundation in hardware,” said Lee Harrison, automotive solutions manager for the Tessent division of Siemens EDA. “The key to system security is to not rely on just one security technology. We refer to this as defense in depth.”
That approach includes:
“Developers building a secure system need to understand that high-level applications (e.g., mobile payments) implicitly rely on the security of ‘lower’ layers,” said Scott Best, director of anti-tamper security technology at Rambus. “For example, a mobile payment app on a phone relies on the integrity of the hypervisor running apps on that phone. And that hypervisor relies on the integrity of the operating system (OS), and the OS relies on the integrity of what’s all the way down at the lowest level/building block of a CPU’s firmware. If the ‘silicon level’ at the foundation of the hardware/software stack isn’t secure, then there’s no chain-of-trust all the way ‘up’ to the mobile payment app.”
Security by design
Because of the increased sophistication of the attacks, building a secure system to defend against these cyber threats is not easy. But with well-defined security goals and advice from cybersecurity experts, cyber defense is achievable.
“Security is not something that you sprinkle on at the end of the design cycle,” said Maarten Bron, managing director at Riscure. “It needs to be baked in right from the beginning. You need certification to go to market, and that is the result of months of development. You also need a good methodology, and an understanding of the hacker’s approach, which is pretty much trying to find the easiest way in. That might be through fault injection to dump the firmware, or reverse engineer the firmware to look for vulnerabilities that allow an exploit.”
In effect, security needs to be integrated into the entire chip design flow. “The first step is to define the security goals,” said George Wall, director of product marketing for Tensilica Xtensa Processor IP at Cadence. “Is doing a secure boot from an authenticated image sufficient? Or are the requirements more stringent? Once those are defined, it becomes possible to define the security architecture and the necessary building blocks. At the most basic level, some support for authentication (e.g., hashing functions) and cryptographic functions is almost always required. SoCs needing to meet more stringent requirements may also have separate secure/non-secure partitions, and even a dedicated security enclave to manage the access to trusted resources.”

Fig. 3: A secure architecture with multiple locks to determine access privilege. Source: Siemens EDA.
The foundation is in the hardware. “Being able to monitor logic-level transactions with an independent architecture is really building security into the DNA of the product,” said Siemens’ Harrison. “This provides a solid foundation of security to build the rest of the solution on top of. Once the foundation is in place, hardware-based secure access is the next step, and with modern root-of-trust solutions, it can provide access to the chip to extract data for analysis. There is a more granular approach to access, giving different levels of access to different parties to increase security. A more open access is assigned for on-premises devices, while a more restricted access is put in place for out-in-the-field devices, which are accessed by a third party. This is implemented and used today.”
Others point to similar approaches. “When building a secure system, you should start from the chip level, as secure products need secure foundations,” said Mark Knight, director, architecture product management at Arm. “Evaluate security frameworks such as PSA Certified, which provide guidance, crowdsourcing expertise, and industry best practices. Any system is only as secure as its weakest component. In most cases, it’s best to start with a certified platform with the broadest possible scope, ideally covering the chip, hardware, and system software. It’s also important to ensure the product is developed under a secure development lifecycle (SDL) that includes threat modeling. This will help identify threats and enable engineers to determine the appropriate mitigations with an acceptable impact on cost.”
Knight identified a number of areas for implementing a secure system, including:
“Modern cybersecurity defense falls into two categories — architectural approaches and security tools,” said Steve Hanna, distinguished engineer at Infineon Technologies. “The architectural approaches address risk management, defense in depth, and zero trust, while tools address strong authentication, secured boot, secured updates, and isolation.”
Hanna pointed to several architectural approaches. One includes risk management, which involves analyzing possible risks and then deciding how to address them. The key here is to focus on the largest risks first — those with the highest probability and and/or high impact. From there, the next step is to figure out how to mitigate those, then move down the list. In all cases, this should involve multiple layers of defense, so that if an attacker gets through one layer, they can be stopped at another. Finally, zero trust is required. It cannot be assumed that something is secure, because hackers can compromise devices and networks while remaining undetected. Users and devices must be authenticated with strong authentication, and they must be monitored for signs of compromise.
That authentication needs to be multi-factor for users, while devices require cryptographic authentication with an asymmetric key. Secure boot, meanwhile, verifies that each piece of the software in the boot sequence is good. If any problems show up, the software needs to be re-installed or reverted to a clean copy. And secure updates need to be verified to ensure they don’t contain malware.
Isolation limits the scope of a compromise. If an attacker compromises one component, isolation will prevent them from getting into another component. For example, firmware and cryptographic keys should be isolated from application software so that infecting the application code won’t damage the firmware or reveal the keys. Isolation can be implemented with a secure element, with separate cores, or with memory protection.
Measuring security
Ultimately, every building block, component, and connection should be secure to achieve end-to-end security. But how do you measure if your systems are secure or not?
“Measuring security does not take place via traditional physical units, such as watts or square feet,” said Lang Lin, principal product specialist at Ansys. “The traditional approach is a pass/fail result or some kind of feasibility study, according to some security compliance test, which is only a rough measure. Moving into the future silicon security sign-off flow, the metric for security should adopt a ‘scoring’ approach, like that used in threat analytics. For example, a ‘leakage score’ for side-channel leakage vulnerability can be used to evaluate the effectiveness of security countermeasures.”
Security metrics are attractive but difficult to implement, in part because security is a moving target and the capabilities of hackers and the effectiveness of security features are constantly in flux.
“Everyone would love some way to indicate when you are 100% secure,” said Mitchell Mlinar, vice president of engineering at Tortuga Logic. “But the complexity of our environment makes it difficult to guarantee complete security. Rather, at each layer, one has to consider the possible weaknesses, such as those defined with a Common Weakness Enumeration (both hardware and software) that can be exploited. One can then determine if these weaknesses are addressed. The challenge is that while one might believe they are 100% secure at that moment, new CWEs are found. The best we can do is resolve all known weaknesses, as well as any other potential weaknesses not part of a CWE. One thing has become very clear — if a weakness exists, no matter how obscure or how unlikely you think it to occur, it will eventually be found and exploited.”
While there is no simple way to measure cybersecurity directly, Dell Technologies offers a free cyber resiliency assessment tool for assessing systems’ security levels. By answering a list of questions, you can receive a report on the vulnerability and exposure of your systems.
Time to take actions
So where to start? “One should first assess the damage to their company’s reputation and to their customers should a malicious attack occur on their product or services — from understanding these potential threats to determining the likelihood that this threat would occur,” said Michael Durkan, senior product architect in Siemens’ Embedded Board Systems Division. “Using these two measures — the potential damage and the risk of occurrence — next determine if a mitigation strategy is necessary to secure one’s products/services against this threat. If mitigation is chosen, the company next must determine the cost of implementing this mitigation strategy. At this point, it becomes a decision process, much like the decision made when taking out insurance. ‘Should I pay this mitigation cost to thwart this particular threat?’ “Of course, there are multiple threats, and when a mitigation process is put in place to deal with a specific threat, then that mitigation process can also be impacted by an attack, typically via a different threat. So the process evolves and becomes one that you continuously evaluate against various threats. As it evolves, you will implement various mitigation policies until the cost of carrying out the threat is sufficiently increased so as to lower the risk of occurrence. At that point the company may decide that the reduced threat risk does not justify the costs of further mitigation. As the Transportation Recall Enhancement, Accountability and Documentation (TREAD) Act passed by Congress in 2000 has demonstrated, mitigation seen as an imposed cost quickly generated cost savings for the industry. For example, the infrastructure surrounding this trusted traceability process has led to better supply chain analysis, improved processes, and fewer product recalls. So when addressing security on products, think of the additional benefits that can be extracted from the implementation of a secured supply chain process.”
Conclusion
Still, while security experts have constantly issued stern warnings about the serious consequences of not having a cybersecurity policy in place, many CEOs and CIOs still lack a sense of urgency about including security in the budget.
“At the end of the day, semiconductors are all about physics,” said Riscure’s Bron. “Physics tells us certain things, like when a gate switches you see power fluctuation, and when a substrate gets excited through a laser or through electromagnetic variances, you may be able to induce bit flips. The laws of physics may sound like a disadvantage when it comes to security, but they’re also an advantage in that same sense. You know what you’re up against. You know what you need to protect against, and that is the same goal post for everybody. It’s riskier for the chip makers and for the good guys than for the bad guys, so you need a very structured approach. You want avoid glitches in your system in the first place, like turning your chip into a Faraday cage or putting a lot of capacitance in there so a voltage glitch will not be able to propagate into the substrate. We can remove a Faraday cage or we can short a cap or disorder it from a PCB. And we can detect any issues at the hardware level in the chip, and to build redundancy into the software. So rather than glitching one conditional branch, you would need to glitch three at the same time to dump a piece of firmware. This is all physics, and you can build countermeasures using it.”
Leave a Reply